What we do

CYBER SECURITY
- Verify & Discover Vulnerabities
- Scan Result & Remediation
- Continuous Monitoring
- Machine Learning

SOC
- Monitoring & Alarms
- Reporting & Analytics
- Security Comms

SECURITY 360
- Assessment
- Identidy Needs
- Personalized Offer
Our partners
Challenge & Mission
- The challenges with information and systems security, especially with a new reality in hybrid telework and increasingly sophisticated threats, are even more difficult to manage and maintain at the level of security and reliability required by organizations.
- Through the technology of our partners and our expert technicians, we aim to help organizations overcome security challenges from a global perspective.
- We provide consulting, analysis, design and implementation services of Network, Security and Cybersecurity solutions in infrastructure and communications.
- LinkCom offer and methodology suited to the reality of your infrastructure.
CSaaS - Cyber Security as a Service
OFFER
- An integrated managed services offering that gives our customers the ability to have a Cybersecurity team to help you maintain data and systems integrity as well as help you address constant threats.
- Through the technology of our partners and our expert technicians, we aim to help organizations overcome security challenges from a global perspective.
RESULTS
- Parameterized services to meet the most emerging needs of organizations.
- Flexibility and availability to integrate the internal offer of organizations.
CSaaS - Cyber Security as a Service
SYSTEMS
- Firewall
- Router/Switches
- Wireless Access Points
- Servers
- Computers
- Printers
- IoT
RESULTS
- Discovery of Assets (Devices & Web Apps)
- Integrated Identification of Assets with Machine Learning
- Scanning of Connected Devices and Equipment
- Security Tests Integrated with Web Applications
- Contextual prioritization conducted by Machine Learning
- Remediation Plan and Risk Assessment Report
“IT Security, a unique, flexible and transversal offer across the various sectors of activity, ensures control and monitoring of the risks and vulnerabilities of on-prem and cloud infrastructures.”
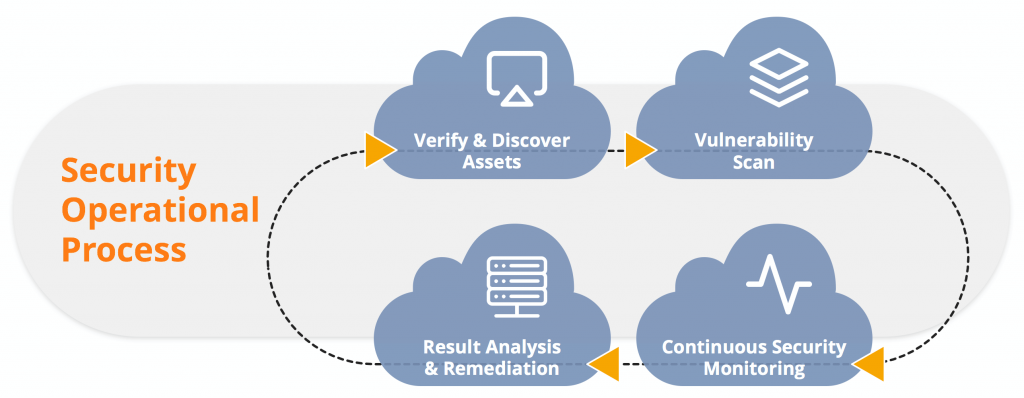
SOC as a Service
LINKCOM SECURITY OPERATIONS CENTER
- Monitoring and Alarms 24/7 Network Activity
- SIEM Tool – Security Information and Event Management
- Reporting and Analytics
- Ticketing
- Support on the CyberSecurity Incident Response Plan (CSIRP)
- Linkcom Security Advisory – Security Communications
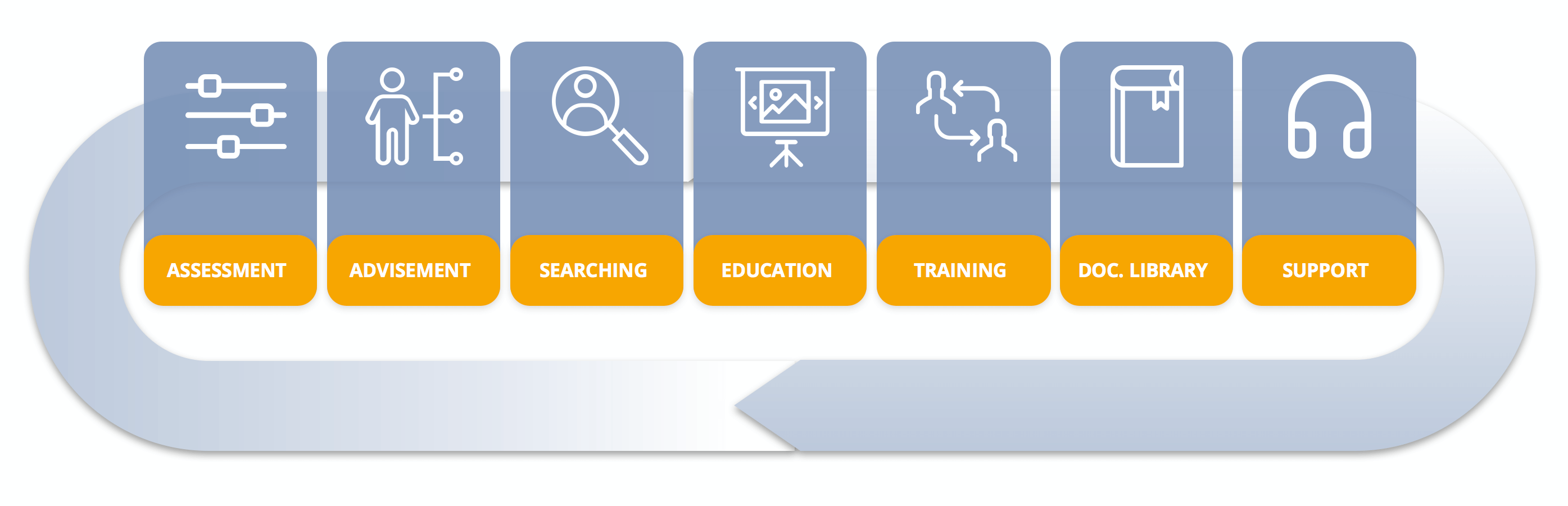
Security 360
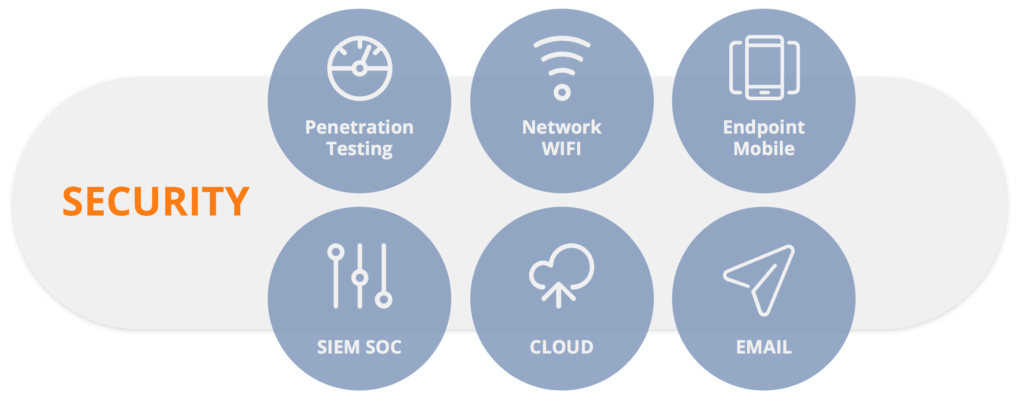
KEY SECURITIES POINTS
- Perimeter Security
- Endpoint and Mobile Security
- Cloud Security
- Network security and WIFI
- Email Security
- Pen Testing
- SIEM / SOC
ACTIONS
- Assessment of customer infrastructure
- Identify key security points to implement or evolve
- Present personalized offer for infrastructure





















